VSS
From Wiki of WFilter NG Firewall
(Difference between revisions)
(Created page with "{{DISPLAYTITLE:Vuln Scan}} == Vuln Scan == "Vuln Scan" is a powerful vulnerability scanning tool capable of detecting a wide range of vulnerabilities across different systems...") |
|||
| (One intermediate revision by one user not shown) | |||
| Line 19: | Line 19: | ||
An additional license is required. Please click "Activate" to install a license. | An additional license is required. Please click "Activate" to install a license. | ||
| − | [[File:vss02.png]] | + | [[File:vss02.png|800px]] |
== Scanning Tasks == | == Scanning Tasks == | ||
| Line 28: | Line 28: | ||
* Schedule, Scheduled run time. | * Schedule, Scheduled run time. | ||
| − | [[File:vss03.png]] | + | [[File:vss03.png|800px]] |
"Tasks" shows the tasks list and status. | "Tasks" shows the tasks list and status. | ||
| − | [[File:vss04.png]] | + | [[File:vss04.png|900px]] |
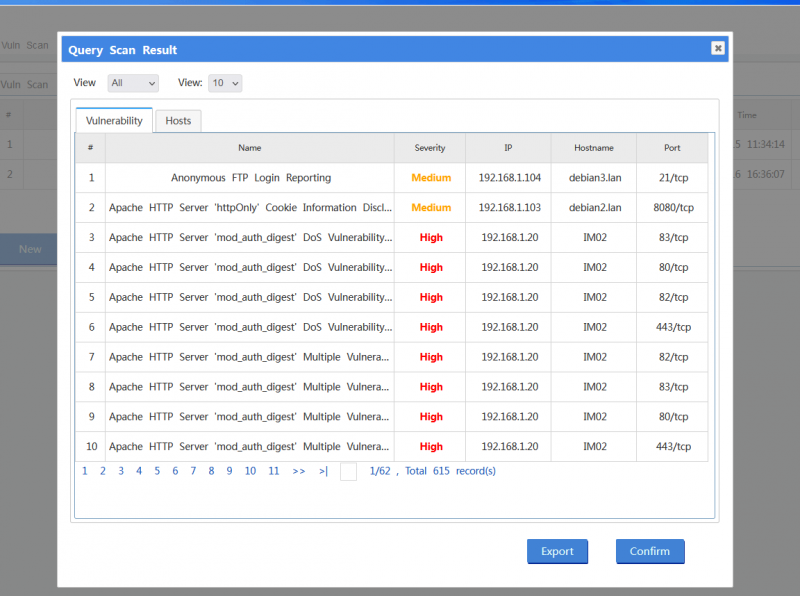
Click the "query" icon to check scanning result. | Click the "query" icon to check scanning result. | ||
| − | [[File:vss05.png]] | + | [[File:vss05.png|800px]] |
= Links = | = Links = | ||
[[Category:Security]] | [[Category:Security]] | ||
Latest revision as of 16:19, 26 August 2024
Contents |
[edit] 1 Vuln Scan
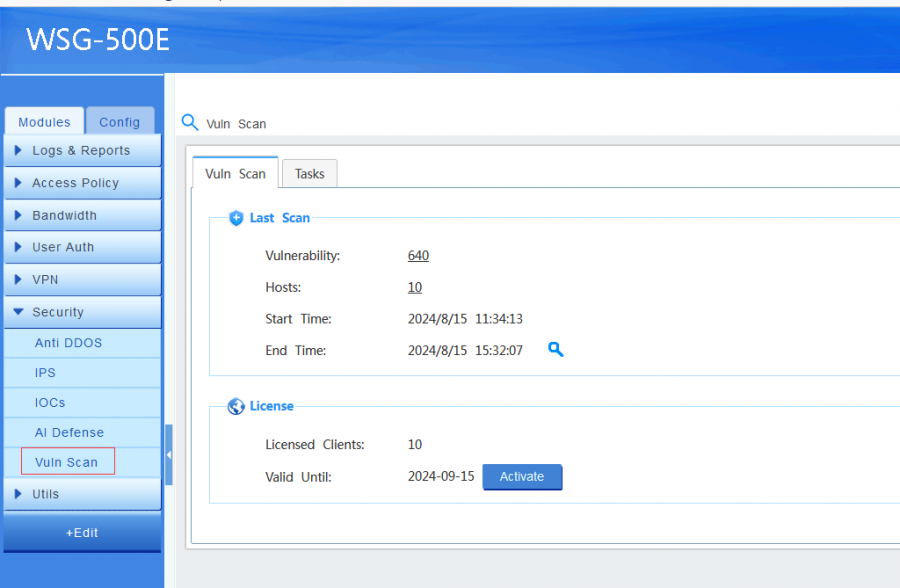
"Vuln Scan" is a powerful vulnerability scanning tool capable of detecting a wide range of vulnerabilities across different systems and networks. Here are some of the types of vulnerabilities can be detected:
- Operating System Vulnerabilities: WFilter can detect known vulnerabilities in popular operating systems such as Windows, Linux, and macOS.
- Application Vulnerabilities: Vulnerabilities in applications can allow attackers to execute malicious code or steal sensitive information.
- Network Device Vulnerabilities: Network devices like routers, switches, and firewalls also have vulnerabilities that can be exploited.
- Web Application Vulnerabilities: Web applications are particularly prone to vulnerabilities like cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF).
- Network Protocol and Service Vulnerabilities: WFilter can scan for vulnerabilities in network protocols and services, such as FTP, SSH, SMTP, and others. These vulnerabilities can allow attackers to gain unauthorized access to systems or data.
- Third-Party Software and Service Vulnerabilities: WFilter also can detect vulnerabilities in third-party software and services, helping organizations take timely remediation measures.
Please notice: the scanning task is initiated from cloud service, which can last up to several hours. Each task will be arranged sequentially.
[edit] 2 License
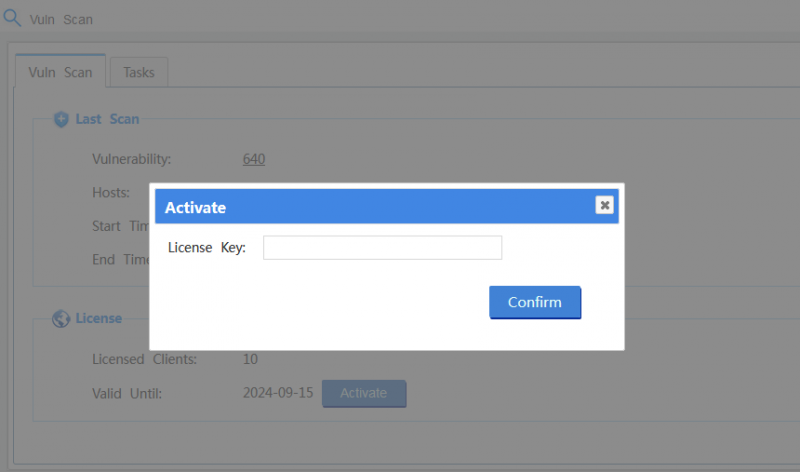
An additional license is required. Please click "Activate" to install a license.
[edit] 3 Scanning Tasks
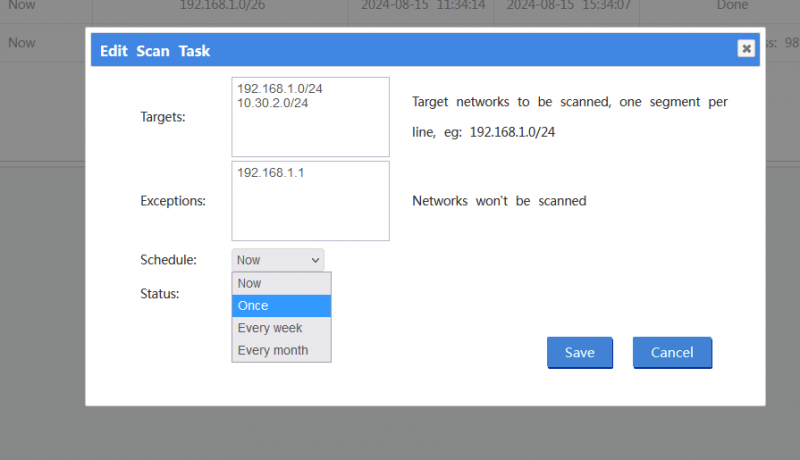
New task settings:
- Targets, target networks, local network only, network mask shall be less than 255.255.255.0(/24), one subnet per line. eg: 192.168.1.0/24
- Exceptions, target networks won't be scanned. one subnet per line. eg: 192.168.1.1/32
- Schedule, Scheduled run time.
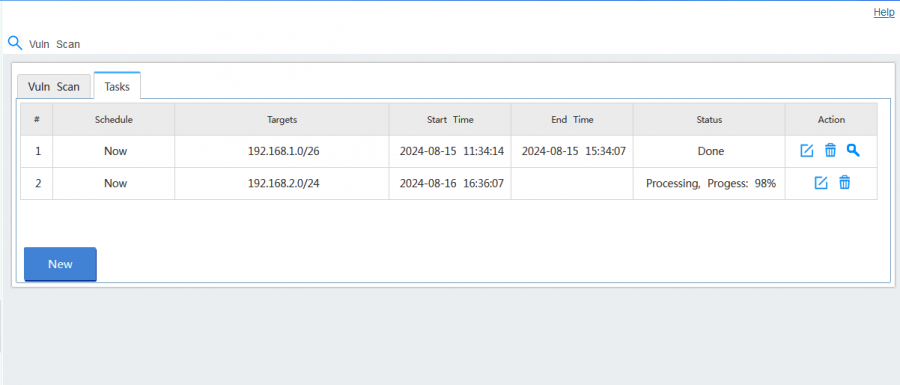
"Tasks" shows the tasks list and status.
Click the "query" icon to check scanning result.