Appcontrol
From Wiki of WFilter NG Firewall
(Difference between revisions)
(→Rule Evaluation) |
(→Rule Evaluation) |
||
| Line 13: | Line 13: | ||
* "Match all" means all rules will be evaluate. A visit will be blocked if any rule blocked it. | * "Match all" means all rules will be evaluate. A visit will be blocked if any rule blocked it. | ||
| − | * "Match first" means only the first matched rule can block access. You can sort rules in this mode. | + | * "Match first" means only the first matched rule can block access. You can sort rules in this mode. For example, in "match first" mode, you can add a "block all" rule to all users. To allow a client, you can add an allow rule, and move this rule to top of the "block all". |
| − | For example, in "match first" mode, you can add a "block all" rule to all users. To allow a client, you can add an allow rule, and move this rule to top of the "block all". | + | |
[[File:ros_appcontrol_03.png|800px]] | [[File:ros_appcontrol_03.png|800px]] | ||
Revision as of 15:35, 12 December 2016
Contents |
1 Application Control
This module enables you to block and allow "applications", also named as "protocols". WFilter identifies each application by digital signature matching, even p2p applications can be completely blocked.
- Each client can be applied with multiple policies.
- Every policy can set "applied to clients" and "effective time".
- Besides the applied to "clients" and "time", detailed "app control policy" settings are described in below.
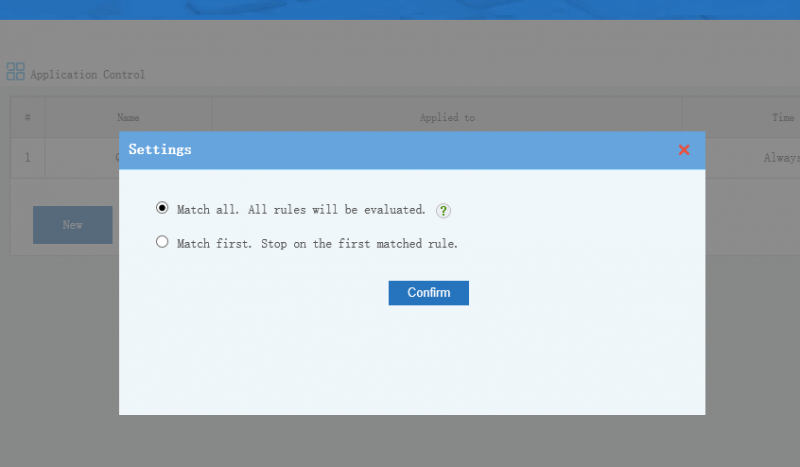
2 Rule Evaluation
- "Match all" means all rules will be evaluate. A visit will be blocked if any rule blocked it.
- "Match first" means only the first matched rule can block access. You can sort rules in this mode. For example, in "match first" mode, you can add a "block all" rule to all users. To allow a client, you can add an allow rule, and move this rule to top of the "block all".
3 Dynamic Filter
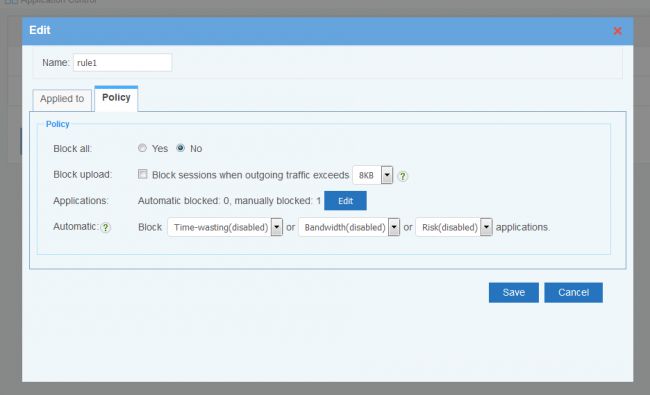
Every application(protocol) has three properties: "time-waisting", "bandwidth" and "risk". With dynamic filter, you can block applications by properties.
- When dynamic filter is enabled, you still can set blocking for each application.
- Every property has 1-5 five levels. For example, bandwidth(5-high) means this application occupies bandwidth in the highest level.
4 Deny and Allow
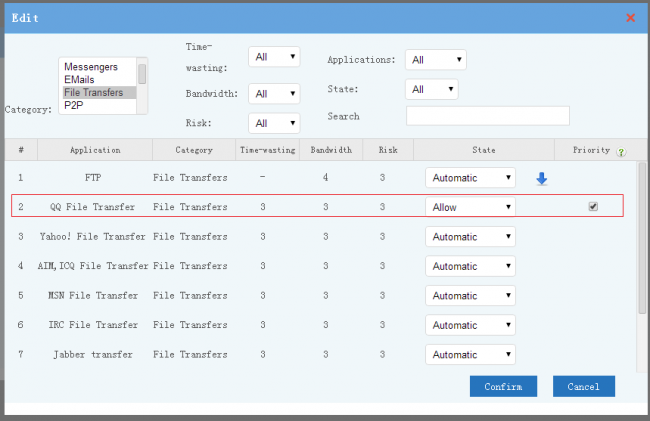
- You may check the applications list and set policy by clicking "edit".
- If "state" is "Automatic", this application will match the "dynamic filter" rule. "Deny" state applications will be blocked. "Allow" state applications will not be blocked.
- Applications with "-" properties won't be matched by "dynamic filter" rule.
- When "Priority" is enabled, this application won't be blocked by other rules or modules. For example, For example, "qq file transfer" is relayed by websites; if you block web surfing, "qq file transfer" will also be blocked unless "Priority" of "qq file transfer" is enabled.