Firewallrule
From Wiki of WFilter NG Firewall
(Difference between revisions)
| (14 intermediate revisions by one user not shown) | |||
| Line 1: | Line 1: | ||
| − | {DISPLAYTITLE:Rules}} | + | {{DISPLAYTITLE:Firewall Rules}} |
| − | == | + | |
| − | + | "Firewall Rules" block or allow traffic based on IP and ports. If you need "URL filter", "application control" and so on, you need to check modules in [[Access_Policy|"Access Policy"]]. | |
| − | + | ||
| − | + | == New Rule == | |
| − | + | [[File: Firewall_set_en.png|650px]] | |
| − | + | ||
| − | + | New a firewall rule, descriptions: | |
| − | + | ||
| − | + | * '''Interface''': "LAN" or "WAN". WAN interface is invalid in bridge mode. | |
| − | + | * '''Type''': packet direction. | |
| − | [[ | + | ** "Inbound", packet targets to the NGF device. |
| + | ** "Forward", packet being forwarded. | ||
| + | * '''Source''': packet source. You can define IP as "Any", "Single", "Range" and "Customize". | ||
| + | ** For "Single", a single ip or subnet is allowed(for example: 192.168.1.10 or 192.168.1.0/24). | ||
| + | ** For "Range", you need to input an ip range. | ||
| + | * '''Target''': packet target, can be "Any", "Single", "Range" and "Customize". | ||
| + | * '''Source Port''': packet source port, can be a single port or a port range, | ||
| + | * '''Target Port''': packet target port, can be a single port or a port range, Syntax: | ||
| + | ** One port: 8000 | ||
| + | ** A port range: 8000:9000 | ||
| + | ** Multiple ports: 80 8000 | ||
| + | ** Port and ranges: 80 8000:9000 | ||
| + | ** Empty matches all ports | ||
| + | * '''Protocol''' | ||
| + | ** All: means all protocols, including TCP, UDP, ICMP and other IP protocols. | ||
| + | ** TCP+UDP: both TCP and UDP. | ||
| + | * '''Action''': | ||
| + | ** "Reject": the rejected clients will get a RST packet immediately. | ||
| + | ** "Drop": packets will be dropped, the clients will wait for connection timeout. | ||
| + | ** "Allow": allow packet | ||
| + | * You may use '''time''', '''from-to''' and '''effective on''' to define a time period for this rule to be applied. | ||
| + | |||
| + | == Customize IP == | ||
| + | |||
| + | Upon "Customize", you can block ip, subnets, countries and regions, domains and domain categories. For domains, WFilter will add dns replied ip addresses into the deny/allow list. | ||
| + | |||
| + | [[File: ros_firewall_dstip01.png|650px]] | ||
| + | |||
| + | [[File: ros_firewall_dstip02.png|650px]] | ||
| + | |||
| + | [[File: ros_firewall_dstip03.png|650px]] | ||
| + | |||
| + | [[File: ros_firewall_dstip04.png|650px]] | ||
| + | |||
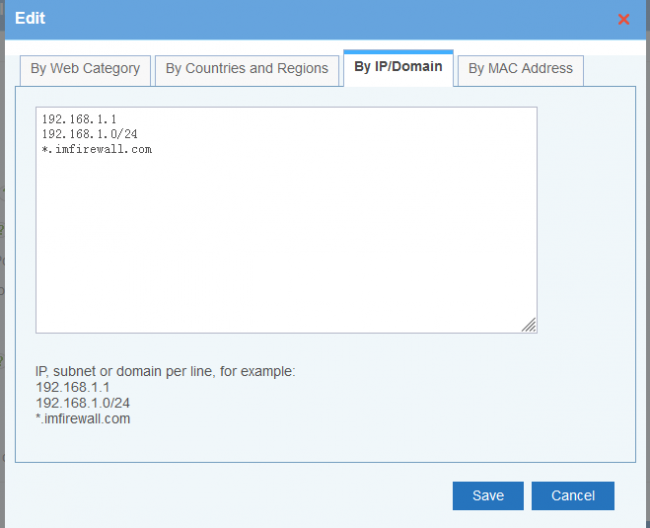
| + | IP, subnet or domain per line, for example: | ||
| + | |||
| + | 192.168.1.1 | ||
| + | |||
| + | 192.168.1.0/24 | ||
| + | |||
| + | *.imfirewall.com | ||
| + | |||
| + | [[File: ros_firewall_dstip05.png|650px]] | ||
| + | |||
| + | == Processing Order for Rules == | ||
| + | |||
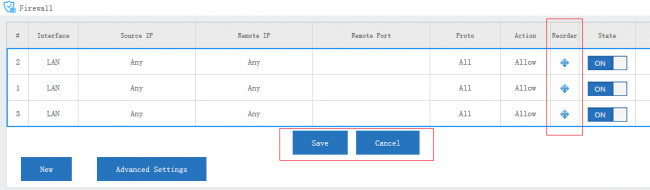
| + | Rules are always processed from the top of a list down, first match wins. Understanding this order is especially important. | ||
| + | You may drag the re-order icon to re-order rules. | ||
| + | |||
| + | [[File: ros_firewall_01.png|650px]] | ||
| + | |||
== Advanced Settings == | == Advanced Settings == | ||
| − | + | ||
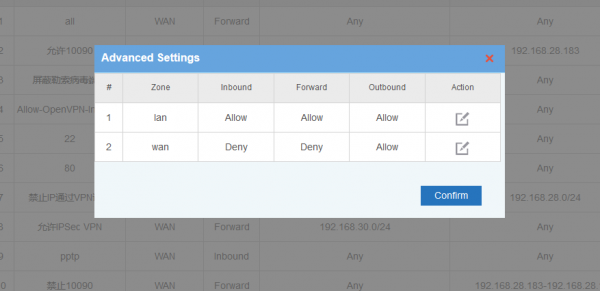
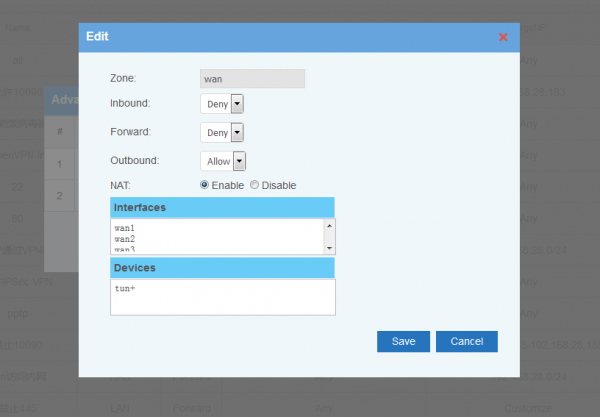
| − | + | In "Advanced Settings", you can setup default policies for ZONEs. Two Zones(LAN and WAN) are supported in default. | |
| − | + | ||
| − | [[ | + | [[File: Firewall_advanced_en.png|600px]] |
| + | |||
| + | [[File: Firewall_advanced_en02.png|600px]] | ||
| + | |||
| + | [[Category:Firewall]] | ||
Latest revision as of 17:01, 20 January 2022
"Firewall Rules" block or allow traffic based on IP and ports. If you need "URL filter", "application control" and so on, you need to check modules in "Access Policy".
Contents |
[edit] 1 New Rule
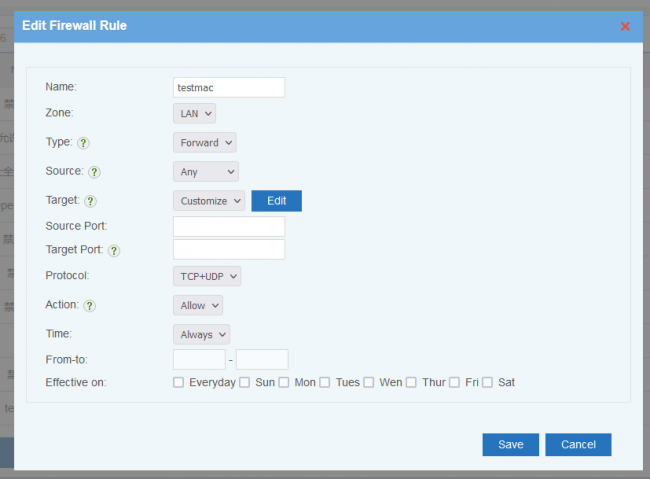
New a firewall rule, descriptions:
- Interface: "LAN" or "WAN". WAN interface is invalid in bridge mode.
- Type: packet direction.
- "Inbound", packet targets to the NGF device.
- "Forward", packet being forwarded.
- Source: packet source. You can define IP as "Any", "Single", "Range" and "Customize".
- For "Single", a single ip or subnet is allowed(for example: 192.168.1.10 or 192.168.1.0/24).
- For "Range", you need to input an ip range.
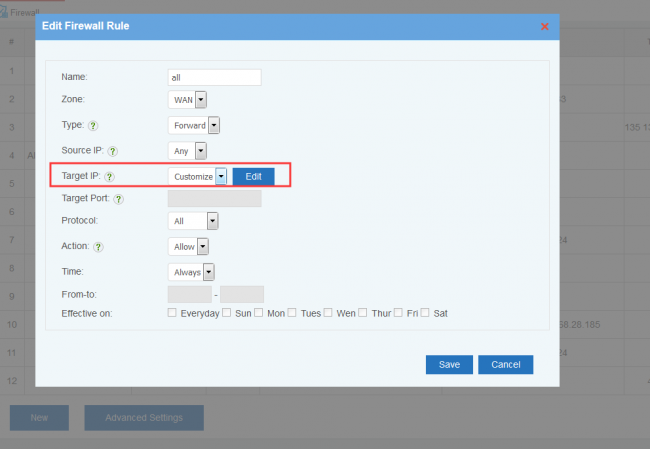
- Target: packet target, can be "Any", "Single", "Range" and "Customize".
- Source Port: packet source port, can be a single port or a port range,
- Target Port: packet target port, can be a single port or a port range, Syntax:
- One port: 8000
- A port range: 8000:9000
- Multiple ports: 80 8000
- Port and ranges: 80 8000:9000
- Empty matches all ports
- Protocol
- All: means all protocols, including TCP, UDP, ICMP and other IP protocols.
- TCP+UDP: both TCP and UDP.
- Action:
- "Reject": the rejected clients will get a RST packet immediately.
- "Drop": packets will be dropped, the clients will wait for connection timeout.
- "Allow": allow packet
- You may use time, from-to and effective on to define a time period for this rule to be applied.
[edit] 2 Customize IP
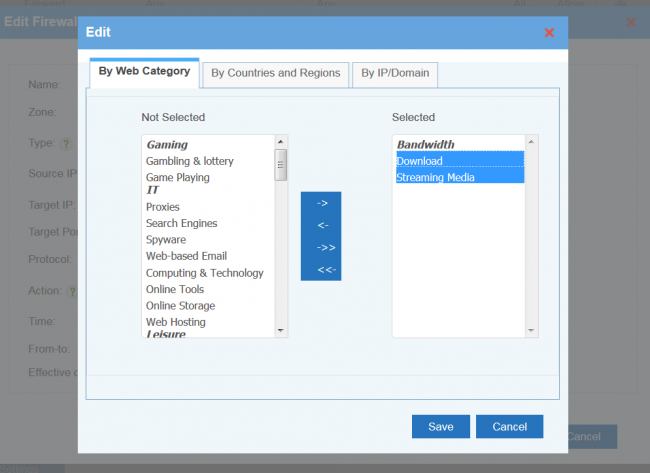
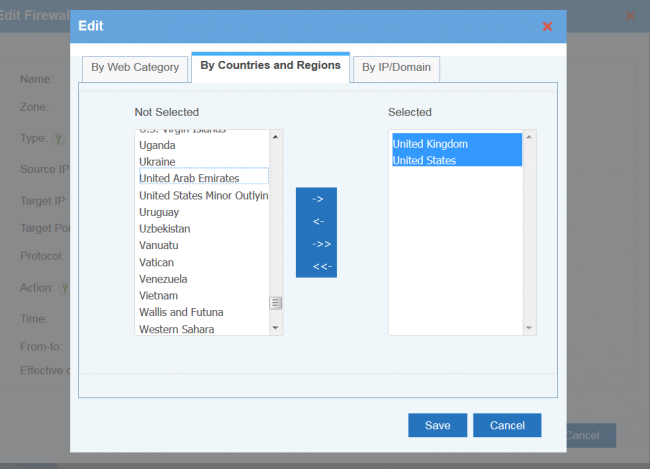
Upon "Customize", you can block ip, subnets, countries and regions, domains and domain categories. For domains, WFilter will add dns replied ip addresses into the deny/allow list.
IP, subnet or domain per line, for example:
192.168.1.1
192.168.1.0/24
- .imfirewall.com
[edit] 3 Processing Order for Rules
Rules are always processed from the top of a list down, first match wins. Understanding this order is especially important. You may drag the re-order icon to re-order rules.
[edit] 4 Advanced Settings
In "Advanced Settings", you can setup default policies for ZONEs. Two Zones(LAN and WAN) are supported in default.