Firewall Rules
From Wiki of WFilter NG Firewall
"Firewall Rules" block or allow traffic based on IP and ports. If you need "URL filter", "application control" and so on, you need to check modules in "Access Policy".
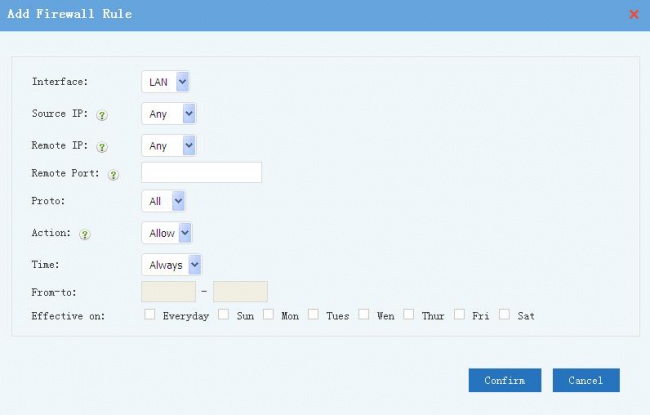
1 New Rule
New a firewall rule, descriptions:
- Interface: "LAN" or "WAN", interface for this rule to work on.
- Source IP: packet source ip address. You can define IP as "Any", "Single" and "Range".
- For "Single", a single ip or subnet is allowed(for example: 192.168.1.10 or 192.168.1.0/24).
- For "Range", you need to input an ip range.
- Remote IP: packet target ip address, same syntax as the "Source IP".
- Remote Port: packet target port, can be a single port or a port range, for example: 8000 or 8000:9000(range).
- Action:
- "Reject": the rejected clients will get a RST packet immediately.
- "Drop": packets will be dropped, the clients will wait for connection timeout.
- "Allow": allow packet
- You may use time, from-to and effective on to define a time period for this rule to be applied.
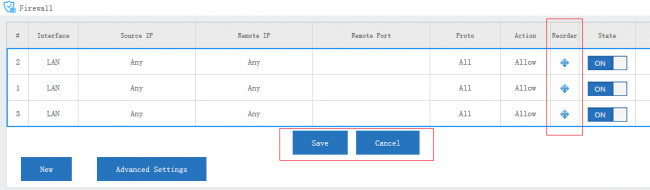
2 Processing Order for Rules
Rules are always processed from the top of a list down, first match wins. Understanding this order is especially important. You may drag the re-order icon to re-order rules.
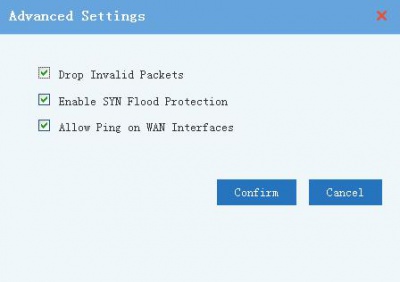
3 Advanced Settings
Some advanced options, recommended to enable.
- Drop Invalid Packets.
- SYN Flood Protection: Kind of DDos attack.
- Allow Ping on WAN Interfaces: Allow ICMP ping to the WAN interface from external network.