IPS Protection
Contents |
1 IPS Protection
IPS(intrusion prevention system) can detect and block attacks from WAN or LAN subnets. This module is built on the Snort project.
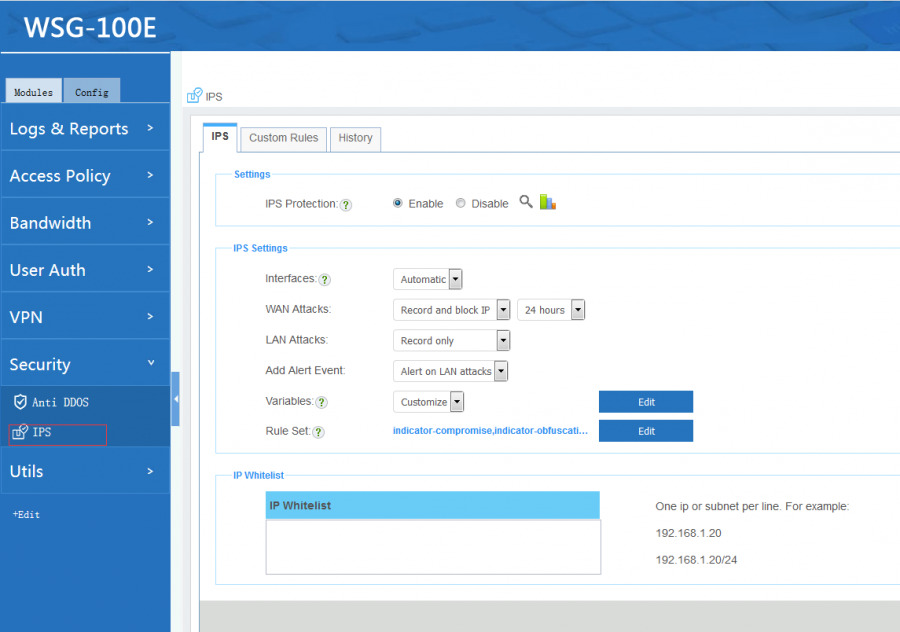
2 Settings
- Interfaces: Packets on the selected interfaces will be analysed and matched against the snort IDS engine. By "automatic", all LAN interfaces will be selected.
- WAN Attacks: setup the policy on attacks from internet.
- LAN Attacks: setup the policy on attacks from LAN subnets.
- Record only, only record the attacks events.
- Record and block ip, record the attack events and block the source ip for a period.
- Ignore, no action on attacks.
- Add Alert Event: whether to add attacks events to the "Event" module.
- Variables: Variables for LAN subnets and ports to be protected. By "automatic", all LAN subnets and common ports will be choosen.
- Rule Set: Define the rules set for detection.
- IP Whitelist: whitelisted traffic won't be checked. Syntax: 192.168.1.20,192.168.1.20/24.
3 Variables
Choose "Customize" and click "Edit", you will be able to configure the "Variables". By "automatic", all LAN subnets and common ports will be choosen. If you want to protect local servers, please add the local servers ip addresses and ports.
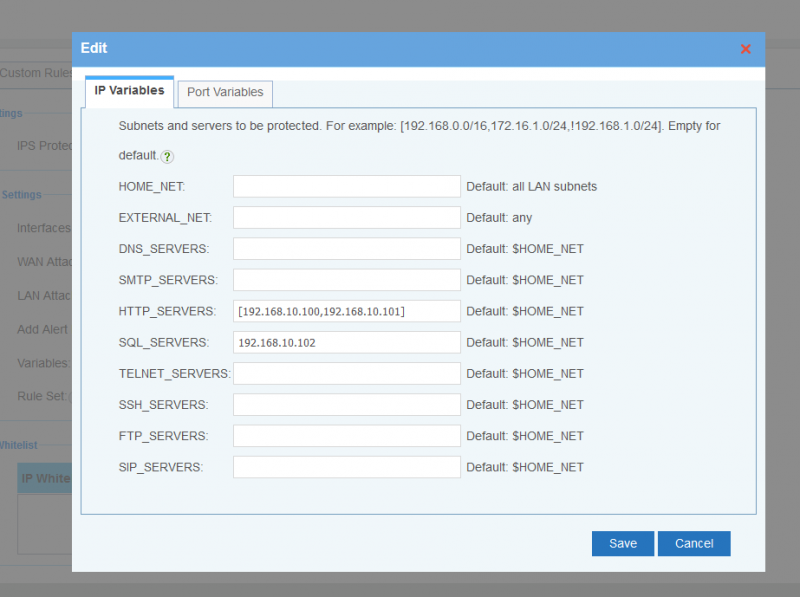
3.1 IP Variables
- Define ip variables for subnets and severs to be protected. You may check snort documents for more details.
- HOME_NET: local LAN subnets to be protected, default is all LAN subnets.
- EXTERNAL_NET: external networks, default is "any".
- DNS_SERVERS: DNS servers to be protected, default is $HOME_NET.
- SMTP_SERVERS: SMTP servers to be protected, default is $HOME_NET.
- HTTP_SERVERS: HTTP web servers to be protected, default is $HOME_NET.
- SQL_SERVERS: database servers to be protected, default is $HOME_NET.
- TELNET_SERVERS: telnet servers to be protected, default is $HOME_NET.
- SSH_SERVERS: ssh servers to be protected, default is $HOME_NET.
- FTP_SERVERS: FTP servers to be protected, default is $HOME_NET.
- SIP_SERVERS: SIP servers to be protected, default is $HOME_NET.
- Syntax(same as snort):
- Single IP or subnet: 192.168.10.0/24
- Multiple IP or subnets:[192.168.10.0/24,192.168.20.0/24]
- ! for exception:[192.168.10.0/24,!192.168.10.100]
- Please note: server ip addresses shall be LAN ip addresses, not public IP addresses.
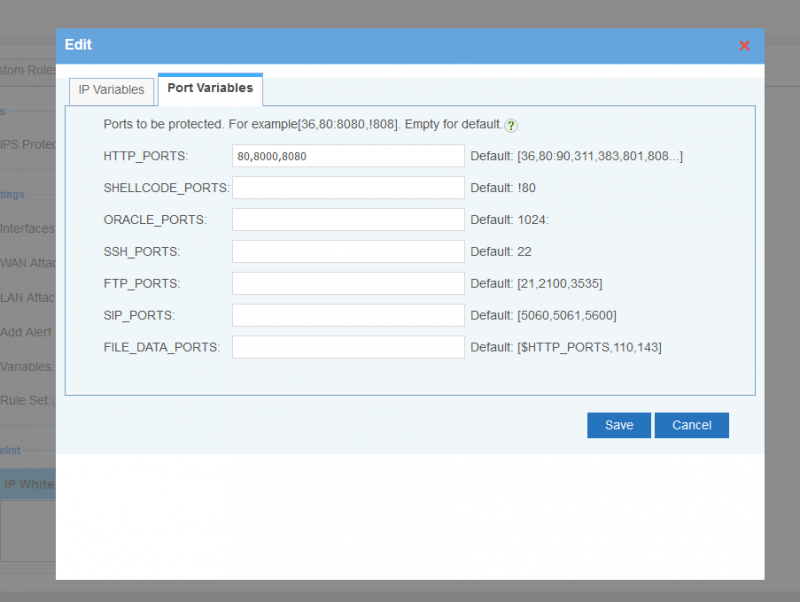
3.2 Port Variables
- Ports to be protected. You may check snort documents for more details.
- HTTP_PORTS: default is [36,80,81,82,83,84,85,86,87,88,89,90,311,383,555,591,593,631,801,808,818,901,972,1158,1220,1414,1533,1741,1812,1830,1942,2231,2301,2381,2578,2809,2980,3029,3037,3057,3128,3443,3702,4000,4343,4848,5000,5117,5250,5450,5600,5814,6080,6173,6988,7000,7001,7005,7071,7144,7145,7510,7770,7777,7778,7779,8000,8001,8008,8014,8015,8020,8028,8040,8080,8081,8082,8085,8088,8090,8118,8123,8180,8181,8182,8222,8243,8280,8300,8333,8344,8400,8443,8500,8509,8787,8800,8888,8899,8983,9000,9002,9060,9080,9090,9091,9111,9290,9443,9447,9710,9788,9999,10000,11371,12601,13014,15489,19980,29991,33300,34412,34443,34444,40007,41080,44449,50000,50002,51423,53331,55252,55555,56712]
- SHELLCODE_PORTS: shellcode port, default is "!80"(all ports except 80)
- ORACLE_PORTS: oracle port, default is "1024:"(1024:65534)
- SSH_PORTS: ssh ports, default is "22".
- FTP_PORTS: FTP ports, default is "[21,2100,3535]".
- SIP_PORTS: SIP ports, default is "[5060,5061,5600]".
- FILE_DATA_PORTS: file tranfer ports, default is "[$HTTP_PORTS,110,143]".
- Syntax:
- Single port, eg: 80
- Multiple ports, eg:[80,8000,8080]
- Port range, eg: 1024:2048
- ! for exception, eg: [1024:2048,!2000]
- Note: ports shall be LAN ports, not the forwarded WAN ports.
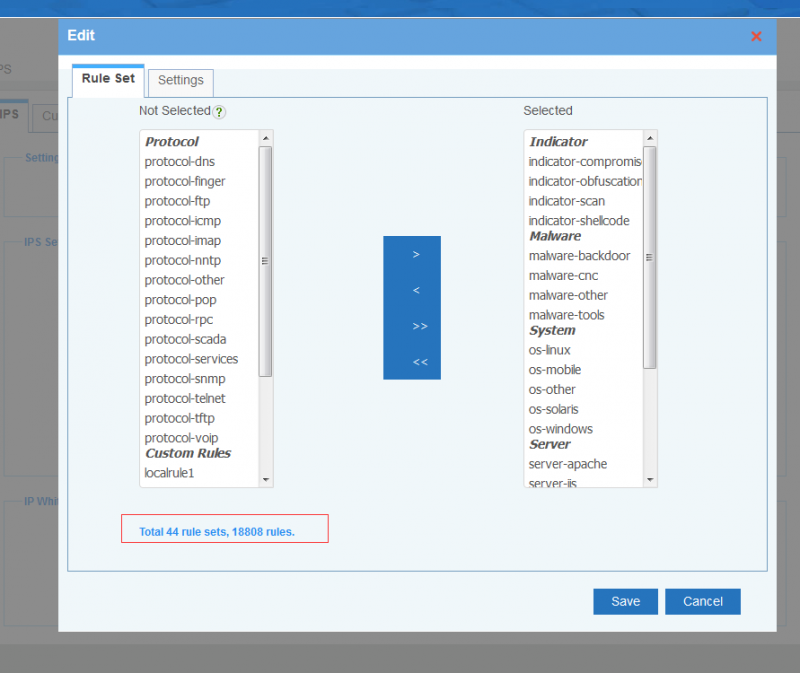
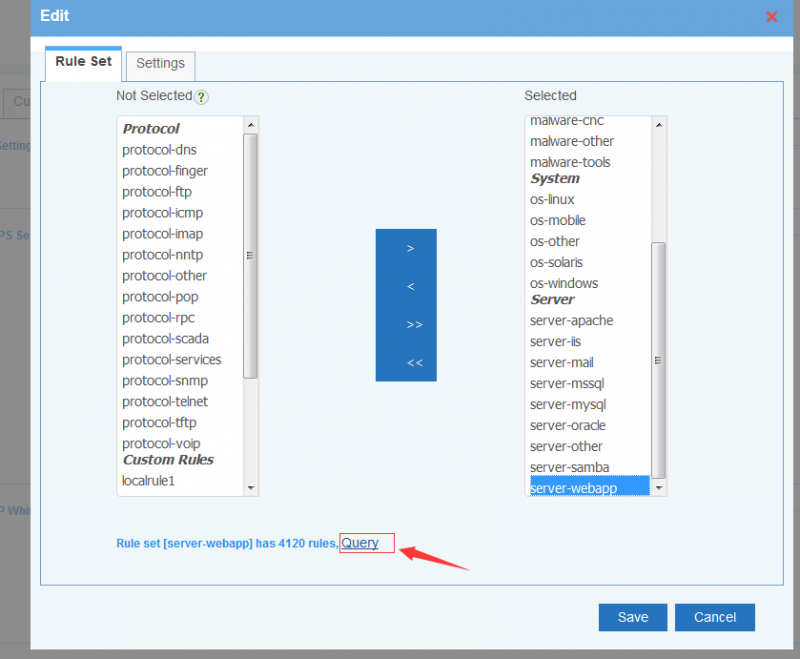
4 Rule Set
Define the rules set for detection. Pre-defined rule sets:
- Indicator: detect local compromised clients.
- Malware: inbound and outbound malware attacks.
- Server: attacks to local services.
- System: attacks to local operation systems./li>
- Protocol: attacks to protocols.
To protect local client devices, please enable "Indicator" and "Malware" rule sets. To protect local servers, please enable "Server", "System" and "Protocol" rule sets.
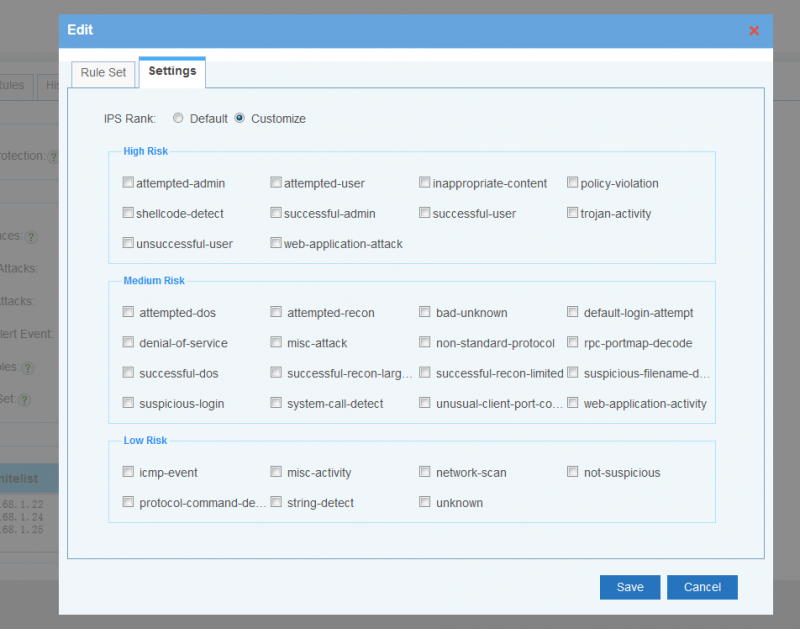
IPS Settings, by default, only recommened rules are enabled.
- "High" means high priority rules, like attempted-admin, shellcode-detect, trojan-activity...
- "Medium" includes actions less harmful, like attempted-dos, non-standard-protocol, suspicious-login...
- "Low" means actions might be harmful, like network-scan, protocol-command-decode...
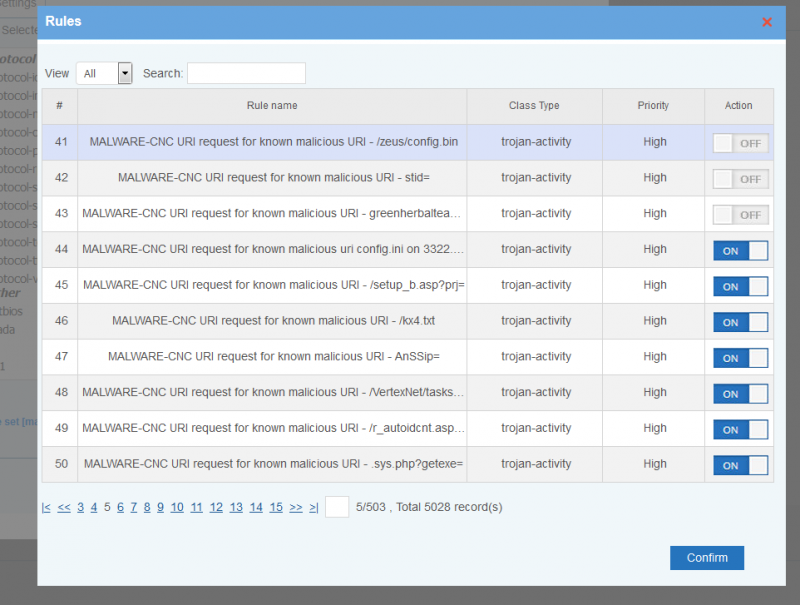
Click each ruleset name, you can check the rules amount and detailed rules.
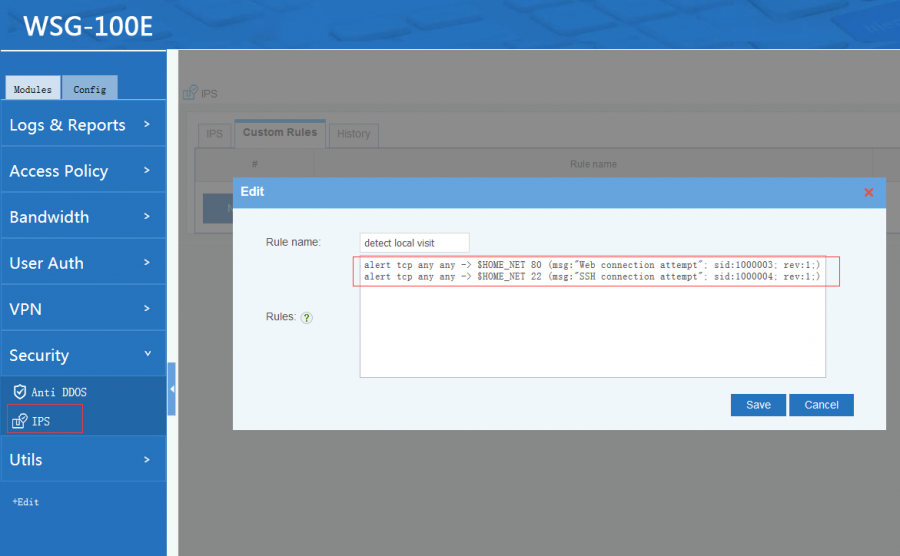
5 Custom Rules
Besides of the system rulesets, you also can define custom rules. The syntax is same as snort:
6 History
Query history records of attack events, including ip addresses, ports, type and messages.