Openvpn
(→Server Settings) |
(→Server Settings) |
||
| Line 9: | Line 9: | ||
= OpenVPN Server = | = OpenVPN Server = | ||
== Server Settings == | == Server Settings == | ||
| − | * Auth | + | * Auth by: "by certificate" or "by user&pass". |
** Users & Pass(recommended): authenticate by user & password, only "local users" with "VPN" privilege have VPN access. | ** Users & Pass(recommended): authenticate by user & password, only "local users" with "VPN" privilege have VPN access. | ||
** Certificate: authenticate by certificate, client need to import the certificate created by the server. | ** Certificate: authenticate by certificate, client need to import the certificate created by the server. | ||
| Line 15: | Line 15: | ||
* Client Subnet: WFilter's openVPN works in "subnet" mode. In this mode, OpenVPN will setup a new subnet, which can not same as existing LAN subnets. | * Client Subnet: WFilter's openVPN works in "subnet" mode. In this mode, OpenVPN will setup a new subnet, which can not same as existing LAN subnets. | ||
* Push Route: The subnets will be pushed to clients routing table, so client can access server's subnets. For example: '''route 192.168.126.0 255.255.255.0''' | * Push Route: The subnets will be pushed to clients routing table, so client can access server's subnets. For example: '''route 192.168.126.0 255.255.255.0''' | ||
| − | * | + | * Auth Type: |
** "Local Auth": authenticate with username and password of local accounts. Only "local users" with "VPN" priviledge have VPN access. | ** "Local Auth": authenticate with username and password of local accounts. Only "local users" with "VPN" priviledge have VPN access. | ||
** "Email Auth": send credentials to a pop/imap email server for authentication. | ** "Email Auth": send credentials to a pop/imap email server for authentication. | ||
Revision as of 20:19, 9 July 2019
Contents |
1 Introduction
- OpenVPN is an open-source software application that implements VPN based on SSL. These two modules can setup OpenVPN tunnels in WFilter NG Firewall.
- OpenVPN Server: provide VPN service for remote access and site-to-site VPN server.
- OpenVPN Client: VPN client to connect other OpenVPN servers.
2 OpenVPN Server
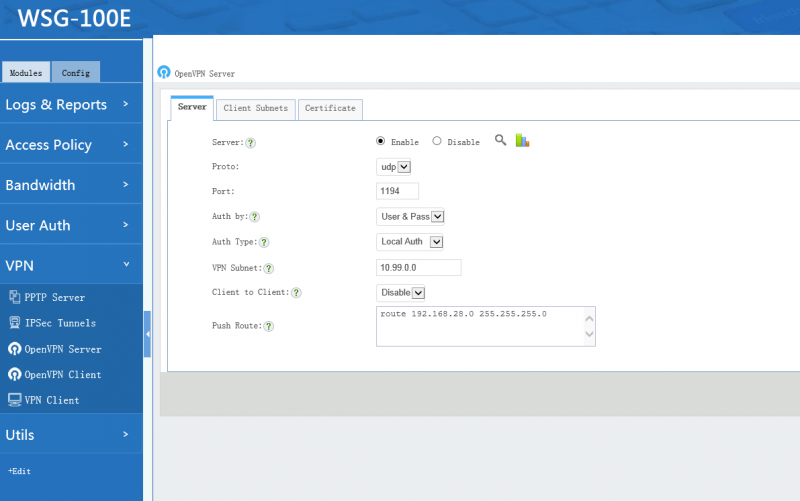
2.1 Server Settings
- Auth by: "by certificate" or "by user&pass".
- Users & Pass(recommended): authenticate by user & password, only "local users" with "VPN" privilege have VPN access.
- Certificate: authenticate by certificate, client need to import the certificate created by the server.
- Protocol and port: connection protocol and port, shall be consistent with the client settings.
- Client Subnet: WFilter's openVPN works in "subnet" mode. In this mode, OpenVPN will setup a new subnet, which can not same as existing LAN subnets.
- Push Route: The subnets will be pushed to clients routing table, so client can access server's subnets. For example: route 192.168.126.0 255.255.255.0
- Auth Type:
- "Local Auth": authenticate with username and password of local accounts. Only "local users" with "VPN" priviledge have VPN access.
- "Email Auth": send credentials to a pop/imap email server for authentication.
- "Ldap Auth": send credentials to a ldap server for authentication.
- "Radius Auth": send credentials to a remote radius server for authentication.
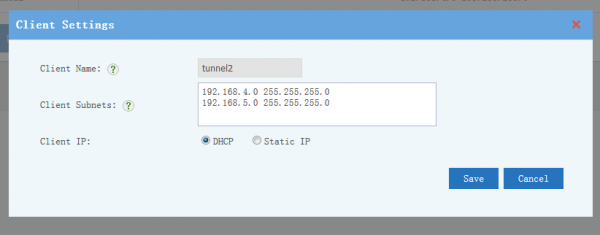
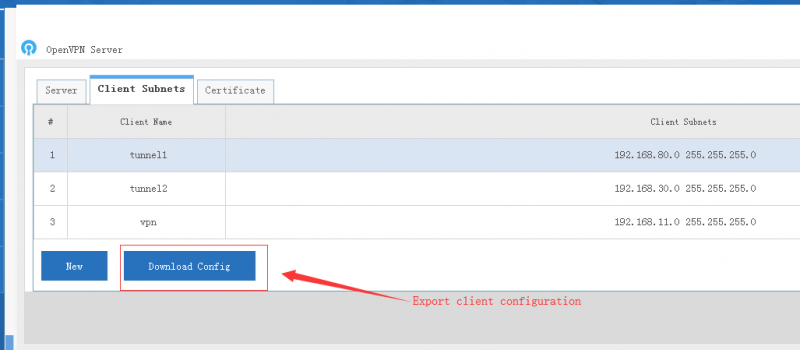
2.2 Client Subnets
- "Client Subnets" defines client subnets for site-to-site VPN.
- "Client Subnets" defines client subnets for server to access client networks. For example: 192.168.126.0 255.255.255.0
- For "Client IP", DHCP is enough for most cases. You also can setup a static ip address for a client, so you can configure firewall ACL rules to limit the accessible resources for this ip address.
- For user & pass authentication clients, the client id shall be client username.
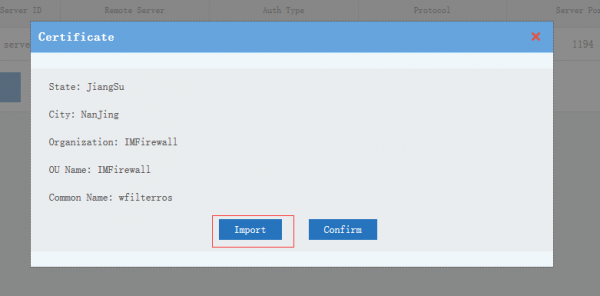
- For certificate authentication clients, you need to download and import the client certificate in client side.
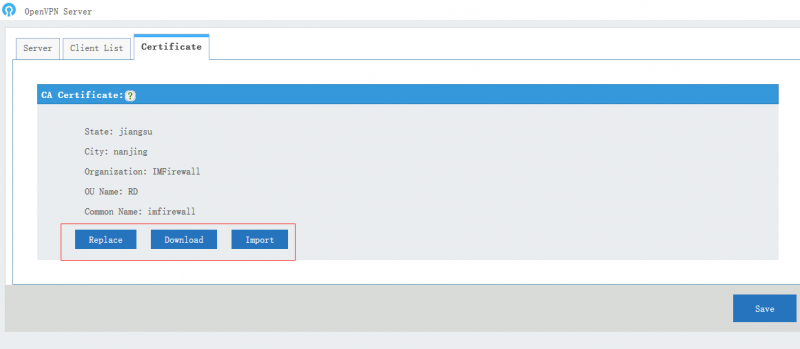
2.3 CA Certificate
- CA certificate: the CA certificate which shall be imported into openVPN client directory, you can click "Replace" to generate a new certificate.
3 OpenVPN Client
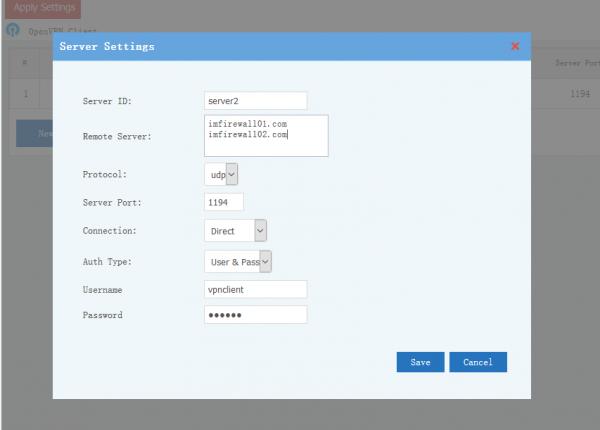
OpenVPN client can connect to multiple OpenVPN servers.
- Server ID:unique server ID, alphabet and numeric charactors only.
- Remote server: remote openvpn server domains or IP addresses. You can have multiple remote entries for load balance between servers. One server per line.
- Protocol and port.
- Proxy: connect to remote proxy OpenVPN server via a HTTP proxy.
- Auth Type:
- User & Pass: Authenticate by username and password.
- Certificate: Authenticate by certificate files created in server.
- CA Certificate
You can check and import CA certificate. A client shall have the server's CA to establish a SSL connection.
3.1 Import certificates from other openvpn servers
WFilter NGF can import the exported certificates from other WFilter systems. However, if you need to import certificates from other openvpn servers, you need to pay attention to the file format and path.
- Import client CA:
- The file format shall be tar.gz.
- File path: /etc/config/openvpn/ca.crt and /etc/config/openvpn/ca.key
- Commands:
$tar -cvzf /tmp/ca.tar.gz /etc/openvpn/ca.*
- Import client certificates:
- The file format shall be tar.gz.
- File path: /tmp/clientkeys/xxx.crt and /tmp/clientkeys/xxx.key
- Commands:
$mkdir -p /tmp/clientkeys
$rm -f /tmp/clientkeys/*
$cp -f client1.crt /tmp/clientkeys/
$cp -f client1.key /tmp/clientkeys/
$tar -czf /tmp/client1.tar.gz /tmp/clientkeys/
4 Windows Clients
- Download and install the offical openvpn client: https://openvpn.net/index.php/open-source/downloads.html
- Download CA certificate in WFilter NG Firewall, copy it to openvpn's config directoy with name "ca.crt".
- Download client configuration.
4.1 User&Pass Clients
- Download the config file into the config directory of openvpn, with file content format:
client dev tun proto udp #Connection protocol, same as the server settings. remote 192.168.1.246 1194 #Server IP(domain) and port nobind persist-key persist-tun ca ca.crt #ca.crt filename, same directory with the myvpn.ovpn verb 3 auth-user-pass #auth by username
4.2 Certificate Clients
- configure file:
client dev tun proto udp #Connection protocol, same as the server settings. remote 192.168.1.246 1194 #Server IP(domain) and port nobind persist-key persist-tun ca ca.crt #ca.crt filename, same directory with the myvpn.ovpn verb 3 cert vpnuser.crt #Exported client certificate key vpnuser.key #Exported client certificate key
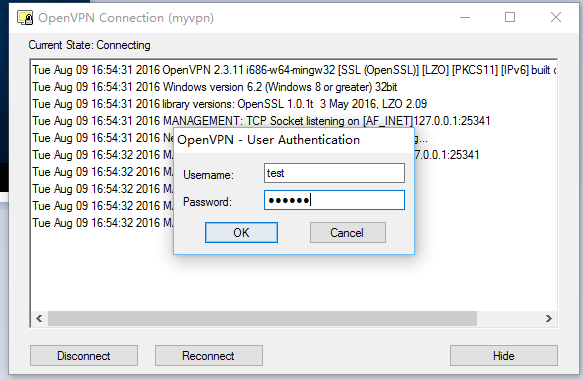
- Now you can launch "OpenVPN GUI" with administrator privilege, input correct username and password to access VPN.
5 Firewall Rules
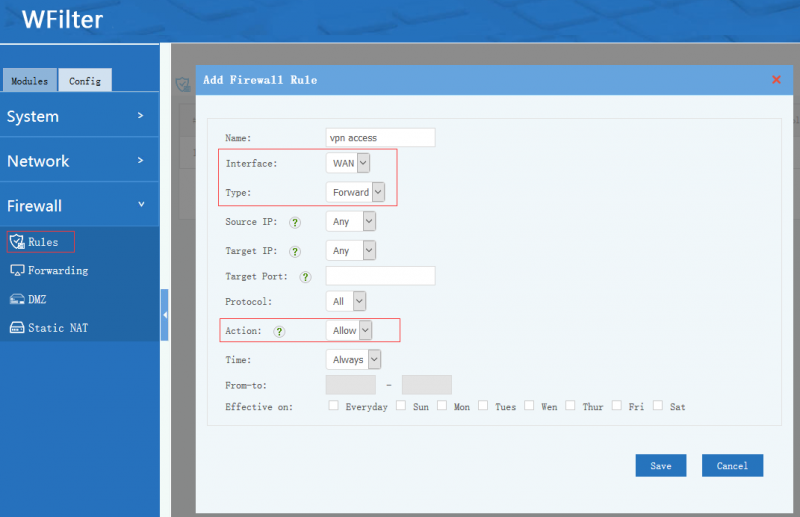
VPN access to LAN is controlled by firewall rules. For example, if you want to allow vpn access to all LAN clients, you need to add a firewall rule(Interface:WAN, Type: FORWARD, Action: Allow):
- Example 1, allow VPN users to access all LAN resources:
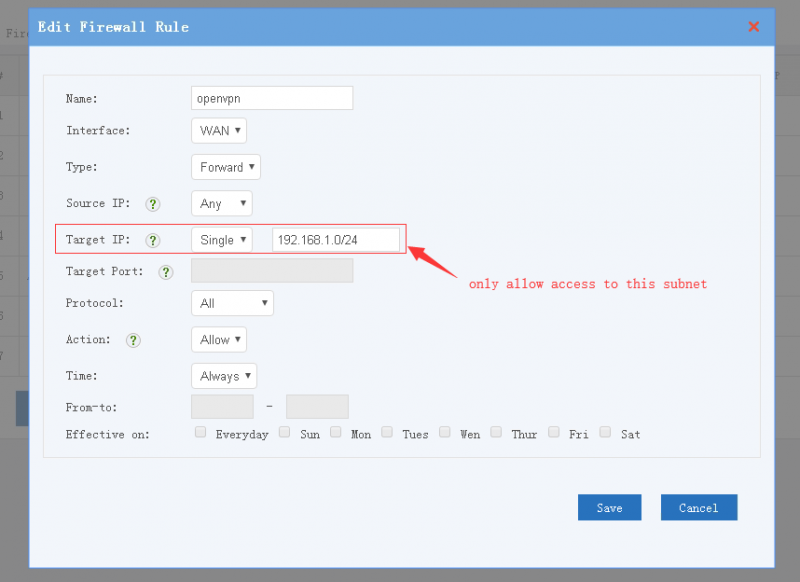
- Example 2, allow access to target subnet only: